How Attackers Can Own a Business Without Touching the Endpoint
1 min read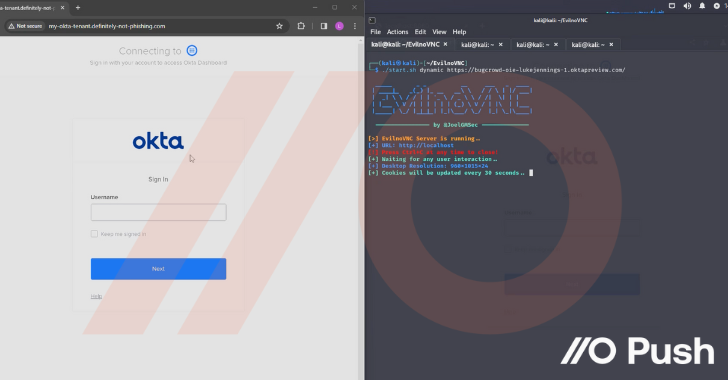
Attackers are increasingly making use of “networkless” attack techniques targeting cloud apps and identities. Here’s how attackers can (and are) compromising organizations – without ever needing to touch the endpoint or conventional networked systems and services.
Before getting into the details of the attack techniques being used, let’s discuss why





